Configuring TLS for MC Users, for Mutual Mode
You can configure TLS for existing MC users who are already mapped to Vertica database user ids. You would do so if you had just configured TLS in mutual mode on a previously unsecured Vertica database, and needed to configure a client certificate and private key for each MC user who accesses that database.
- In MC, navigate to MC Settings and click the User Management tab.
- Select a user from the list and click Edit.
- In the Add permissions window:
- Choose the database for which you want to edit this MCC user's security permissions.
- MC displays the database username to which this MC user is currently mapped.
- In the Restrict Access drop-down, choose Admin, Associate, IT, or User to specify the privilege level for this user.
- In the Use TLS Connection drop-down, choose Yes.
- Click Configure TLS for user to launch and complete the Certificates wizard.
MC Certificates Wizard
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server. Each screen presents options. When you select an option, the wizard displays additional options and details. Screenshots below represent one version of what you may see.
- Read the first screen and click Configure TLS Certificates to continue.
-
On the Configure CA Certificates screen, configure a CA certificate (public key) to add to MC's trust store. MC uses this trusted certificate to verify the server's identity during TLS communications over JDBC connections between MC and the Vertica database server.
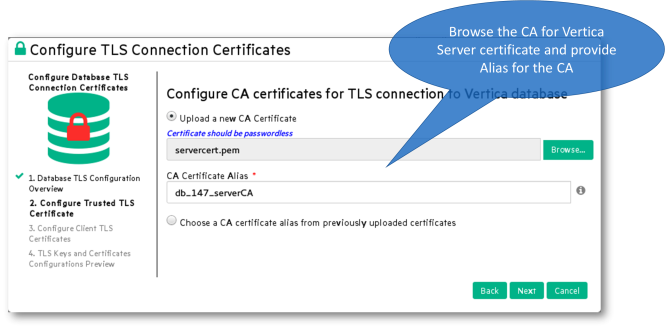
Complete one of these options:
- Upload a new CA certificate by browsing and selecting the PEM file, then enter an alias for this certificate (shown above).
- Choose an alias from a list of previously uploaded certificates.
- Click Next.
- The Configure Client Certificate screen displays the check box Add Client Certificate and Private Key for Mutual Mode TLS Connection.
- If the database is configured for server mode, you don't need a client certificate or key.
- Leave the Add Client Certificate check box unchecked and click Review.
- Go to step 8.
-
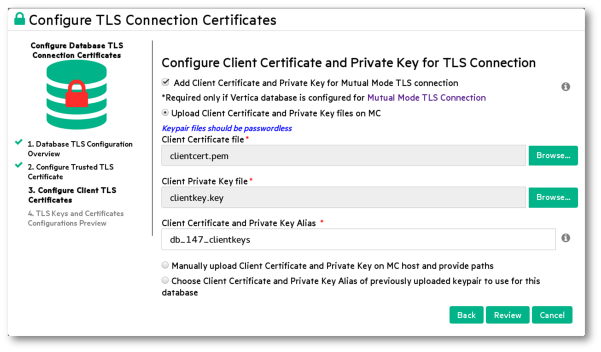
If the database is configured for mutual mode, click the check box, then select one of these options. Complete the detail fields for that option:
-
Upload Client Certificate and Private Key files on MC (shown above.) MC uses its https connection from the browser to MC's host to upload the files.)
-
Manually upload client Certificate and Private Key on MC host and provide paths (Avoids sending encrypted certificate and private key files over an https connection.)
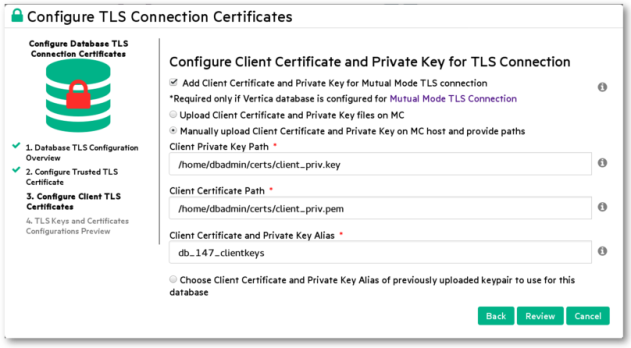
- Choose Client Certificate and Private Key alias of previously uploaded keypair to use for this database. (To use existing certificate and key files.)
-
- Click Review. The wizard displays a review window with the TLS options you have configured.
- If you are importing a database, choose one of these options:
- To modify your TLS choices, click Back.
- To confirm your choices, click Configure TLS and Import DB. The wizard displays success messages. Click Close to complete the wizard.
- To close the wizard without importing the database and without setting up TLS configuration, click Cancel.
- For all other use cases, click Close to complete the MC Certificates wizard.