
This blog post was authored by Soniya Shah.
If you find yourself, as the Vertica database administrator, locked out of your database account, it usually happens for one of two reasons: either youve forgotten your password, or your authentication is not working. Either way, this can be a frustrating situation. This blog discusses how you can customize authentication methods in Vertica.
You can use a number of different authentication methods, including Ident, Kerberos, LDAP, and hash. If you only have one authentication method associated with your user, dbadmin or otherwise, Vertica uses that method to authenticate your login attempt. To help prevent a situation where your authentication does not work, our security team at Vertica has a few recommendations.
Assigning Hash Authentication
First, as the dbadmin, you can change the priority of any authentication method. You should assign the highest priority to at least one of the hash authentication methods you intend to use. If you dont currently use hash authentication, you can learn more by visiting the Hash Authentication page in the Vertica documentation.
Assigning LDAP Authentication
Second, if you choose to use LDAP authentication, set up more than one LDAP authentication method because you could encounter issues if the LDAP server goes down. If the server is down, your login attempts will fail. Setting up another authentication method might not be helpful because if the LDAP-type authentication fails, Vertica only looks for other LDAP-type authentication methods. To avoid having all login attempts fail, you can set up more than one LDAP authentication method. That way, if one fails, Vertica can try to authenticate the user against a second LDAP server. For more information, see LDAP Authentication in the Vertica documentation.
Using Multiple Authentication Methods
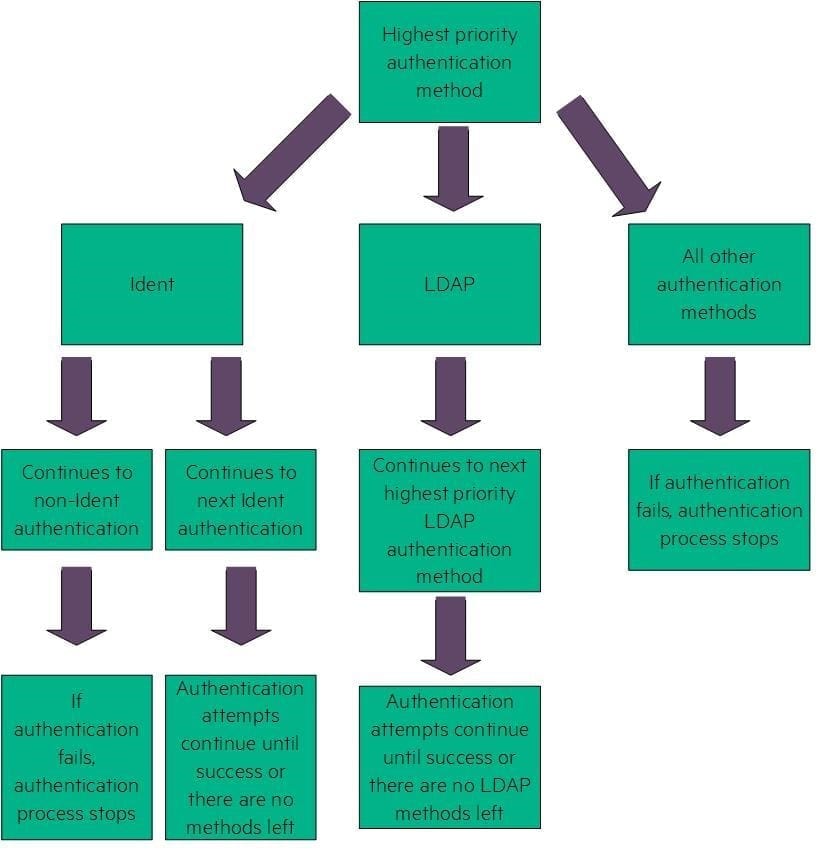
Third, if you have multiple authentication methods assigned to your user, be sure that you understand how priority for these methods works. If the first method fails, you might not be able to fall back on a different method, depending on what your first method was. Vertica follows the authentication attempts described in Priorities for Client Authentication Methods in the Vertica documentation.
The following diagram illustrates these attempts in more detail. Based on your highest priority authentication method, Vertica follows these attempts to authenticate:
Lastly, if you assign an authentication method to the PUBLIC role, it affects all users, including the superuser. Its always a good idea to have a different authentication method to fall back on!






